What is MITM Attack?
MITM is also called Man in the middle attack. Friends, this attack of hackers is called Middle Man Attack, someone means a person in the middle. The work of this attack is similar. In this hacking technique, a black hat hacker is sitting between two people and accessing the data of both the people before them, then reading the draft and changing it, then sending it to the next person. A man in the middle attack allows a malicious actor to intercept, send and receive data meant for someone else, or not meant to be sent at all, without either outside party knowing until it is too late. Suppose a hacker needs your bank’s confidential information, then he can easily get that information from man using these middle attack. You will not notice that when you have handed over your bank account information to a hacker with your own hands.
To perform the MITM attack here we will use zAnti App. First of all, you know about zAnti App.
zANTI –the hacker tool for android app
zANTI is a penetration testing toolkit developed by Zimperium Mobile Security for cyber security professionals. So today I will give you step by step guide about Zanti, how it is installed and how its various features are performed. So let’s see below which features Zanti supports.
- Change device’s MAC address
- Create a malicious WiFi hotspot
- Hijack HTTP sessions
- Capture downloads
- Modify HTTP requests and responses
- Exploit routers
- Audit passwords
- Check a device for shellshock and SSL poodle vulnerability
{MUST READ : How To Change IMEI Number On Android Device?}
How to install zANTI tool on Android Device?
Step2; Your Android phone must be rutted before this process starts. if your mobile is not rooted then don’t worry just read this post “How To Root Any Android Device?“
Step3; Now you open the Zanti App, after which the screen will open, enter your email address and tick it in the box next to “I accept Zimperium’s EULA”. Then click on “Start Now”.
Step4; Now you will be asked to join the network then tap on “Enable” Or click on “Skip” and wait for few seconds.
Step5; Now after this a screen will open, in which you simply have to tap on “skip” and after this, to enable Zanti, you must tick “I am fully authorized to perform test testings on the network”. And now you click on the finish.
Zanti App is successfully installed on your Android phone, now you can easily perfom with any attack, so friends can see.
Friends, here we will learn to change the image of the website in Victim’s browser, So guys let’s start the attack-
How to perfom man in the middle attack Using zANTI
Step 1; Open the zanti app, You will now see some networks. Just select your target network.
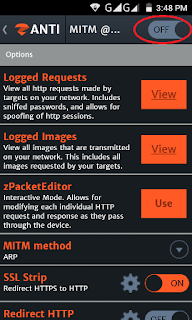
Step2; After selecting Target Network, a new screen will open, in which you click on the MAn In the middle attack.
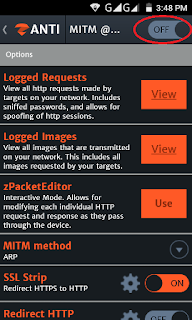
Step3; You will see that when the man in the middle attack screen will open, click on the MITM to turn it on.
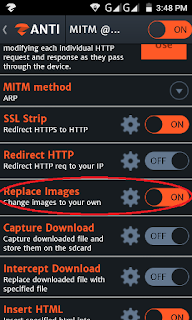
Step4; Now you scroll down in the same screen and go to the Replace Image settings , then select the image you want to show, and turn it on.
the target network you attacked on has become successful, when your victim surf the website from a browser, then he will see the same image that you selected in your phone.
How can you protect the man in the middle attack?
Encryption :
Encryption secures our data to a great extent. Because if we encrypt a document, file, picture, or any type of data, then it changes into a computer language (binary language). Meaning if any of the decryption is opened to him, then it will be visible in both digits 0 and 1, which can be understood only by the computer, not the person.
Mutual Authentication :
If you want the hacker to not read or change your message then you can use the manual authentication. With this you will share whatever data you share with others, they will only see you both.
Digital Signature:
Just like encryption, digital signature is a great way to keep your data safe .You can create your digital signature from any trusted third party site. For this, you will need to scan the retina and fingerprint which will act as a digital signature.
Password:
If your data is not so secret then you can just keep it safe by putting a password. Because in most cases the middle man is attacked when the data is quite secret or appropriate.
Be Sure Before Clicking:
If you come to email or text messages from any company or site first, then after the fact that something like this has happened and the message has come from the real company, it is only after getting the full information that the link is opened.If you also suspect that email is spam, then do not open that link and do not share your intelligence passwords with anyone.
Now here is the end of the article this is overall information for you. Don’t forget to share this post. share it on facebook or any social sites . Thank you so much.