Hello friends once again welcome here in this advance hacking blog. Now today i am going to talk about “Honeypot” If you belong to ethical hacking, cybersecurity, then read this article to the last.
What is Honeypot?
A honeypot is a computer system that is set up to act as a decoy to lure cyber attackers and to detect, deflect or study attempts to gain unauthorized access to information systems.
Generally, ahoneypot consists of data ( like as a network site) that appears to be a legitimate part of the site , but is actually isolated and monitored and that seems to contain information or a resource of value to attackers, who are then blocked.
This is similar to the police baiting a criminal, conducting undercover surveillance and finally punishing the criminal.
A honeypot is a security resources who’s value lies in being probed, attacked or compromised.
Honeypots are weapons against spammers, honeypot detections systems are spammer-employed counter-weapons. As detection systems would likely use unique characteristics of specific honeypots to identify them. A suspected employee of a company can be identified by Honey Pot, his activities can be tracked.
READ MORE:
- [Google Assistant] What is Google Assistant | Everything You Need to Know About Google Assistant ?
- [Facebook Hacking] How to create facebook phising page And How to hack facebook account using phising page?
- Twitter new amazing features in 2018 | How to use Twitter account in new features?
- List of Best Android Apps in 2018 | MyTeachWorld
Honey Pots can be setup inside , outside or in the DMZ of a firewall design or even in all of the locations although they are most often deployed inside of a firewall for control purposes. In a sense , they are variants of standard IDS(intruder detection system) but with more of a focus on information gathering and deception.
Type of honeypots:
Honeypots can be classified based on their deployment(use/action) and based on their level of involvement. Based on deployment, honeypots may be classified as:
- Production Honeypots
- Research Honeypots
Production Honeypots: Production honeypots are easy to use , capture only limited informations and are used primarily by corporations. Production honeypots are placed inside the production network with other production servers by an organization to improve their overall state of security. Normally , production honeypots are low interaction honeypots, which are easier to deploy. They give less information about the attacks or attackers than research honeypots.
Research Honeypots: Research Honeypots are run to gather information about the motives and tactics of the black hat community targeting different networks. These honeypots do not add direct value to a specific organization; instead, they are used to research the threats that organizations face and to learn how to better protect against those threats. Research honeypots are complex to deploy and maintain, capture extensive information, and are used primarily by research, military or government organizations.
Based on design criteria, honeypots can be classified as:
1. Pure Honeypots
2. High-interaction honeypots
3. Low-interaction honeypots
How To Set Up Honeypot On Kali Linux Step by Step follow me?
To set up HoneyPots, a tool will need a tool called pentbox in kaliLinux
Step1; First you have to download the paintbox tool whose link is given below.
git clone https://github.com/whitehatpanda/pentbox-1.8
Step2; Now after downloading the tool simply execute this command cd pentbox-1.8 and hit enter button.
Step3; Now give this command ls for going to the pentbox folder.
Step4; Now you well see a ruby script called pentbox.rb and you need to execute this script by entering this given below command and press enter button.
./pentbox.rb
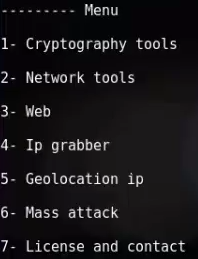
Step5; Now you will show options in terminal window , you need to choose option no. 2 which is network tools. So type the no. 2 and press enter button.
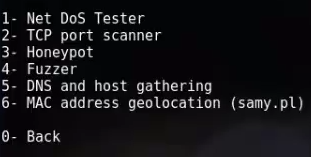
Step6; Now After that again some option you’ll see simply choose option no. 3 which is honeypot.So type no. 3 in terminal and press enter button.
Step7; Now Here you’ll need to choose a option two options Auto configuration and second one is manual configuration. So Choose any one of them according to your need but here i m choosing auto configuration mode.
Step8; So for auto configuration enter 1 and you’ll see that the honeypot will start on port no. 80 or anything which can active for monitor your system.
Step9; Now for checking that honeypot set up working or not simply copy your ip address by executing given below command and enter that ip in any of your web browser and press enter.
ifconfig
So after entering the ip address go towards the terminal windows and here now you’ll see the full detail of the hacker.
If you want to know the actual ip of the victim or the hacker so you just need to make your ip static and send it to anyone if someone click on that link all his information automatically copied in your system in log format.If you can make your ip static then trace anyone all over the worlds with this simple honeypot method.
So guys this is the basic set up of any honeypot solution. If you liked this post, please do not forget to share it, without your support, I can not reach this knowledge even further, so help me by sharing my post so that I can bring you a tricks more than one To share the post ,you can use the share buttons given below, and , If you face some problem in any steps please drop your email by going to contact us section of this site. thank you so much ,stay tune with this blog and blog’s admin Mr. Aditya Singh